How to Conduct Security Risk Assessment for HIPAA Compliance
How to Conduct Security Risk Assessment for HIPAA Compliance

Nearly every American healthcare organization faces the growing challenge of safeguarding patient data as cyber threats rise each year. The stakes have never been higher, with a single data breach costing an average of $10.93 million in the United States alone. For cybersecurity managers, strong security risk assessments are more than just a checkbox for HIPAA compliance—they are crucial for earning patient trust and protecting organizational reputation. This guide breaks down practical steps to strengthen your assessment process and better defend sensitive information.
Table of Contents
- Step 1: Define Assessment Scope And Assemble Your Team
- Step 2: Identify Assets And Analyze Potential Threats
- Step 3: Evaluate Existing Controls And Detect Vulnerabilities
- Step 4: Assess Risk Likelihood And Impact For Each Scenario
- Step 5: Implement Mitigation Strategies And Verify Outcomes
Quick Summary
| Key Insight | Explanation |
|---|---|
| 1. Assemble a diverse assessment team | Include IT, compliance, clinical, and executive members for well-rounded security insights. |
| 2. Document all ePHI systems | Create an exhaustive inventory of systems that handle electronic protected health information. |
| 3. Analyze and quantify threats | Develop a threat scoring matrix to prioritize risks based on likelihood and potential impact. |
| 4. Evaluate existing security controls | Assess current security measures for effectiveness and identify gaps that need attention. |
| 5. Implement and verify strategies | Act on mitigation plans and regularly monitor their success to secure electronic patient data. |
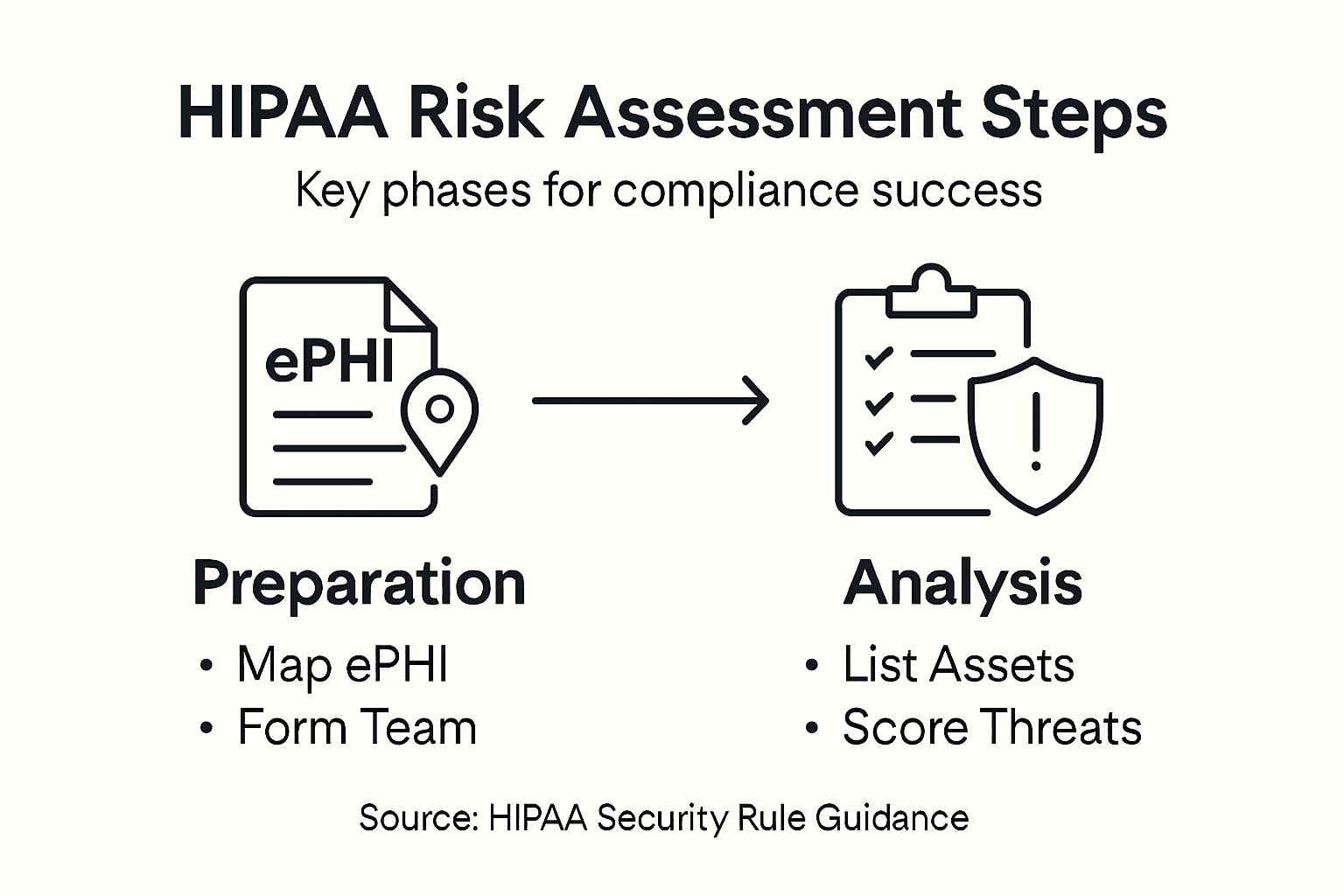
Step 1: Define assessment scope and assemble your team
Defining the assessment scope and assembling the right team are foundational steps in conducting a comprehensive HIPAA security risk assessment. Your goal here is to create a systematic approach for identifying and analyzing potential security vulnerabilities across your healthcare organization.
Start by mapping out your entire electronic protected health information (ePHI) ecosystem. This means creating a detailed inventory of all systems, networks, devices, and locations where patient data is stored, transmitted, or accessed. Comprehensive risk assessment guidelines recommend documenting every electronic system that interacts with patient information. Your inventory should include electronic medical record systems, email platforms, mobile devices, cloud storage solutions, and any third-party applications handling sensitive data.
Building your risk assessment team requires strategic selection of professionals with diverse expertise. You will want representatives from IT, compliance, clinical operations, and executive leadership. Aim for a cross functional group that understands both technical infrastructure and regulatory requirements. Include individuals who comprehend HIPAA security rule requirements and can provide insights into operational workflows.
Pro tip: Consider creating a responsibility matrix that clearly defines each team member's role and expected contributions during the risk assessment process to ensure accountability and comprehensive coverage.
Here is a summary of key team roles and their unique contributions to a HIPAA security risk assessment:
| Team Role | Unique Contribution | Business Impact |
|---|---|---|
| IT Specialist | Technical system and network analysis | Identifies technical vulnerabilities |
| Compliance Officer | Regulatory alignment and documentation | Ensures adherence to HIPAA standards |
| Clinical Operations | Workflow and data flow insight | Improves process security and real-world effectiveness |
| Executive Leadership | Resource and risk prioritization | Supports decision making and accountability |
Step 2: Identify assets and analyze potential threats
Identifying your electronic protected health information (ePHI) assets and analyzing potential threats form the critical foundation of a robust HIPAA security risk assessment. This step involves creating a comprehensive inventory of all systems that interact with sensitive patient data and understanding the various risks those systems might face.
Begin by conducting a thorough systematic inventory of IT assets across your healthcare organization. Document every hardware device, software application, network infrastructure component, and data storage system that touches electronic patient information. This includes desktop computers, mobile devices, servers, cloud platforms, electronic medical record systems, email servers, and any third-party applications that handle patient data. Your goal is to create a detailed map of all potential entry points where protected health information could be vulnerable.

Next, analyze potential threats across administrative, physical, and technical domains. HIPAA security rule requirements mandate a comprehensive threat assessment that considers both external and insider risks. Look for vulnerabilities such as unauthorized access attempts, potential malware infections, insider threat risks, environmental hazards that could compromise data infrastructure, and potential system configuration weaknesses. Consider scenarios like employee errors, accidental data exposure, sophisticated cyber attacks, and physical security breaches that might compromise patient information.
Pro tip: Create a threat scoring matrix that quantifies each identified risk based on potential impact and likelihood of occurrence to prioritize your mitigation strategies effectively.
The table below compares common categories of risks to ePHI during a risk assessment:
| Risk Category | Example Threats | Potential Impact on ePHI |
|---|---|---|
| Administrative | Policy gaps, human errors | Data leaks from mismanaged processes |
| Physical | Theft, disasters | Loss or destruction of data hardware |
| Technical | Malware, hacking | Unauthorized access or data corruption |
Step 3: Evaluate existing controls and detect vulnerabilities
Evaluating existing security controls and detecting potential vulnerabilities is a critical phase in your HIPAA risk assessment. This comprehensive review will help you understand the current state of your electronic protected health information (ePHI) security and identify areas that require immediate attention or improvement.
Begin by conducting a thorough security controls assessment across all administrative, physical, and technical domains. Review your current policies, workforce training programs, access control mechanisms, encryption protocols, and facility security measures. Examine each control systematically to determine its effectiveness in protecting patient data. Pay close attention to authentication processes, data transmission security, workforce access levels, and the implementation of privacy safeguards. Look for potential weak points such as outdated software, inadequate employee training, insufficient access restrictions, or gaps in monitoring and logging systems.
As you evaluate controls, focus on identifying both obvious and subtle vulnerabilities. HIPAA security rule requirements mandate a comprehensive approach that goes beyond surface level checks. Consider potential insider threats, external attack vectors, and systemic weaknesses that might compromise patient information. Use a combination of interviews, technical examinations, and document reviews to create a holistic view of your current security posture. Document every potential vulnerability you discover, noting its potential impact, likelihood of exploitation, and immediate mitigation strategies.
Pro tip: Develop a standardized vulnerability scoring system that helps you prioritize and track identified security gaps, ensuring no critical risks slip through the cracks.
Step 4: Assess risk likelihood and impact for each scenario
Assessing the risk likelihood and potential impact is a critical step in your HIPAA compliance risk management strategy. This process transforms your identified vulnerabilities into a structured approach for prioritizing and addressing security threats to electronic protected health information (ePHI).
Begin by developing a comprehensive risk assessment methodology that systematically evaluates each identified vulnerability. Create a scoring matrix that considers two primary dimensions: the probability of a threat occurring and the potential consequences if it does. For likelihood, consider factors such as historical breach data, current security controls, system complexity, and existing vulnerabilities. Assess potential impact across three key dimensions of ePHI: confidentiality (unauthorized disclosure), integrity (data manipulation), and availability (system accessibility).
Apply a quantitative approach to risk scoring by assigning numerical values to both likelihood and impact. HIPAA security rule requirements emphasize the importance of documented, rational risk prioritization. Use a scale typically ranging from 1 to 5 for both likelihood and impact, creating a risk matrix where overall risk is calculated by multiplying these two scores. High risk scenarios (scoring 16-25) demand immediate mitigation, moderate risks (scoring 6-15) require planned interventions, and low risks (scoring 1-5) can be monitored with existing controls.
Pro tip: Create a color coded risk matrix with clear visual indicators to help leadership quickly understand and communicate the most critical security vulnerabilities.
Step 5: Implement mitigation strategies and verify outcomes
Implementing mitigation strategies is the critical phase where your risk assessment transforms into actionable security improvements for protecting electronic protected health information (ePHI). Your objective is to systematically address identified vulnerabilities and establish robust controls that minimize potential security risks.
Begin by developing a comprehensive risk management approach that prioritizes mitigation strategies based on your previously established risk scoring. Focus on implementing administrative, physical, and technical safeguards tailored to your specific organizational context. This might involve updating security policies, enhancing access controls, implementing advanced encryption protocols, conducting targeted workforce training, and upgrading technological infrastructure. Prioritize high risk scenarios first, allocating resources and attention to the most critical vulnerabilities that could potentially compromise patient data.
After implementing mitigation strategies, establish a rigorous verification process to validate the effectiveness of your interventions. HIPAA Security Rule mandates continuous monitoring and assessment of security controls. Conduct periodic testing, such as penetration testing, vulnerability scans, and security audits, to confirm that your implemented strategies successfully reduce identified risks. Document all mitigation efforts, test results, and ongoing monitoring activities to demonstrate compliance and maintain a comprehensive record of your security improvement initiatives.
Pro tip: Create an automated tracking system that provides real time updates on mitigation strategy effectiveness and alerts leadership to any emerging security gaps.
Strengthen Your HIPAA Compliance with Expert Security Risk Assessments
Conducting a detailed HIPAA security risk assessment is essential for protecting sensitive electronic protected health information and meeting strict regulatory demands. If you are facing challenges like identifying vulnerabilities, evaluating controls, or prioritizing risk mitigation as described in the article, Stonos Solutions is here to help. Our experienced cybersecurity team specializes in delivering thorough risk assessments, vulnerability analyses, and tailored risk management strategies that align perfectly with HIPAA security rule requirements.
Don't wait until vulnerabilities turn into breaches. Partner with Stonos Solutions to enhance your administrative, physical, and technical safeguards today. Visit Stonos Solutions to learn how our expertise in penetration testing, compliance support, and security system optimization can secure your healthcare organization. Take the next step now and safeguard your patients' data with confidence.
Frequently Asked Questions
What are the key steps to conduct a HIPAA security risk assessment?
To conduct a HIPAA security risk assessment, start by defining the assessment scope and assembling a diverse team of experts. Then, identify and document all assets interacting with electronic protected health information (ePHI), analyze potential threats, evaluate existing controls, assess risk likelihood and impact, and finally implement and verify mitigation strategies.
How do I map out my ePHI ecosystem effectively?
To map out your ePHI ecosystem, create a detailed inventory of all systems, networks, devices, and locations storing, transmitting, or accessing patient data. Include electronic medical record systems, email platforms, and third-party applications to ensure comprehensive coverage in your documentation.
What roles should I include in my risk assessment team?
Include professionals from IT, compliance, clinical operations, and executive leadership to create a well-rounded risk assessment team. Each member should contribute unique insights based on their area of expertise, enhancing the overall understanding of both technical and compliance aspects of the assessment.
How can I analyze potential threats to ePHI?
Analyze potential threats by evaluating vulnerabilities in administrative, physical, and technical domains. Use methods such as systematic inventory checks and threat scoring matrices to rate each identified vulnerability based on impact and likelihood, prioritizing those that need immediate attention.
What should I consider when assessing the impact of risks?
Assess the impact of risks by considering the consequences on the confidentiality, integrity, and availability of ePHI. Use a scoring matrix to quantify each risk and prioritize them for mitigation based on their potential impact and likelihood of occurrence.
How do I ensure that my mitigation strategies are effective?
Verify the effectiveness of mitigation strategies by conducting periodic testing, such as security audits and vulnerability scans. Document all results and perform reassessments to ensure ongoing compliance and improvement in protecting ePHI.
Recommended
Louis Romano
Need Security Consulting?
Our expert team is ready to help you enhance your security posture.
Contact Us Today Download Capability StatementRelated Articles
Security Consulting for Integrators: Enabling Resilience
Security Consulting for Integrators: Enabling Resilience ! Consultant briefing integrators in glass-walled office Nearly half of all American healthcare and government organizations face unexpected gaps in their risk management strategies each year.
Read MoreTop 7 Penetration Testing Tools for Small Business 2026
Top 7 Penetration Testing Tools for Small Business 2026 ! Small business IT team meeting for penetration testing Small businesses face new cyber risks every year and smart protection becomes more important with each challenge.
Read More