Top 7 Penetration Testing Tools for Small Business 2026
Top 7 Penetration Testing Tools for Small Business 2026

Small businesses face new cyber risks every year and smart protection becomes more important with each challenge. Finding the right penetration testing tool can be the difference between peace of mind or unexpected problems. Some tools offer powerful reports, others give flexible scanning, and a few even bring automation to the table. The variety might surprise you. Curious about which tools stand out and what sets them apart for smaller companies? Explore how different solutions might fit your business goals and your budget.
Table of Contents
- Stonos Solutions
- Rapid7 Platform
- Tenable One Exposure Management Platform
- CrowdStrike Falcon Platform
Stonos Solutions
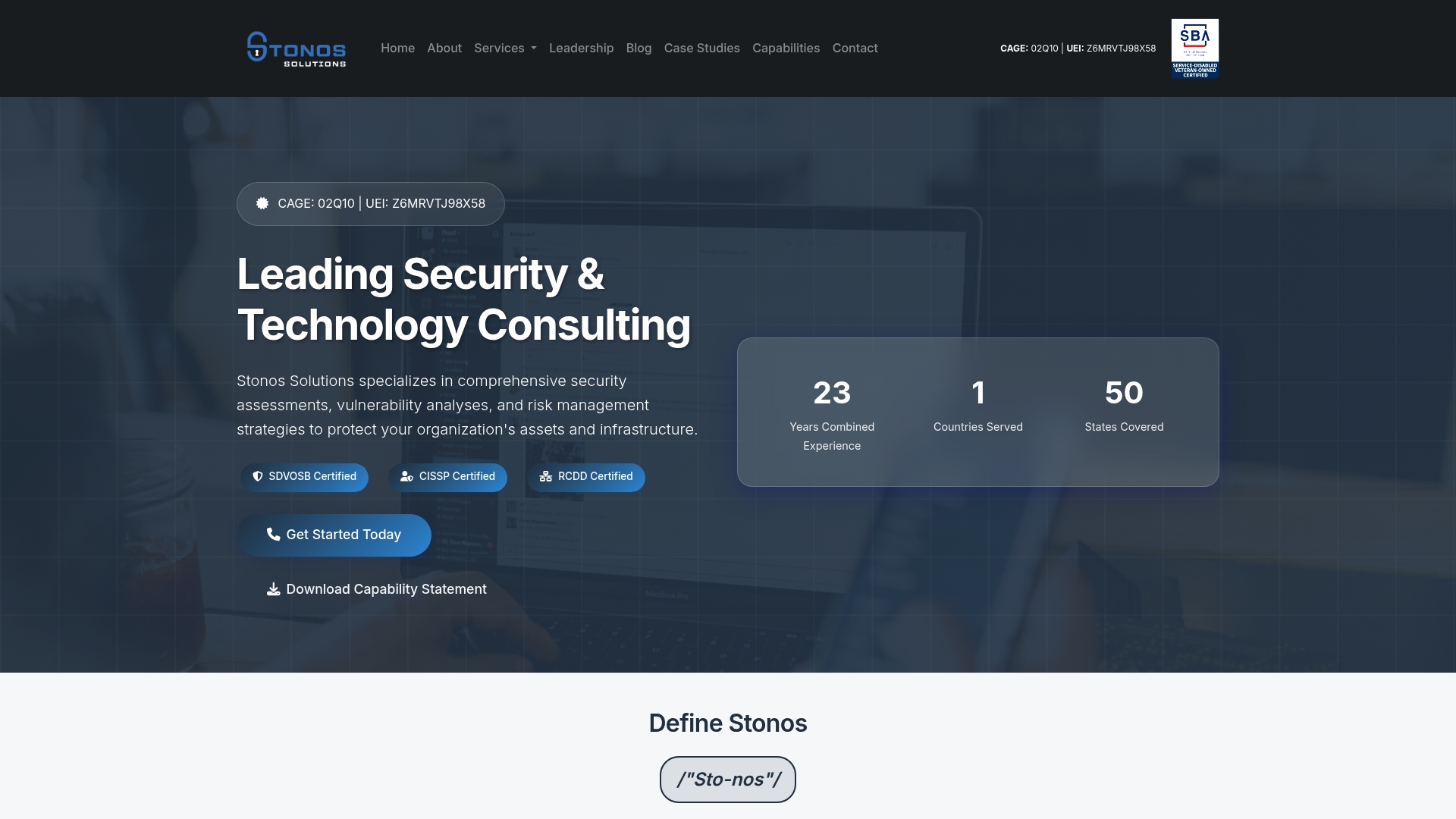
At a Glance
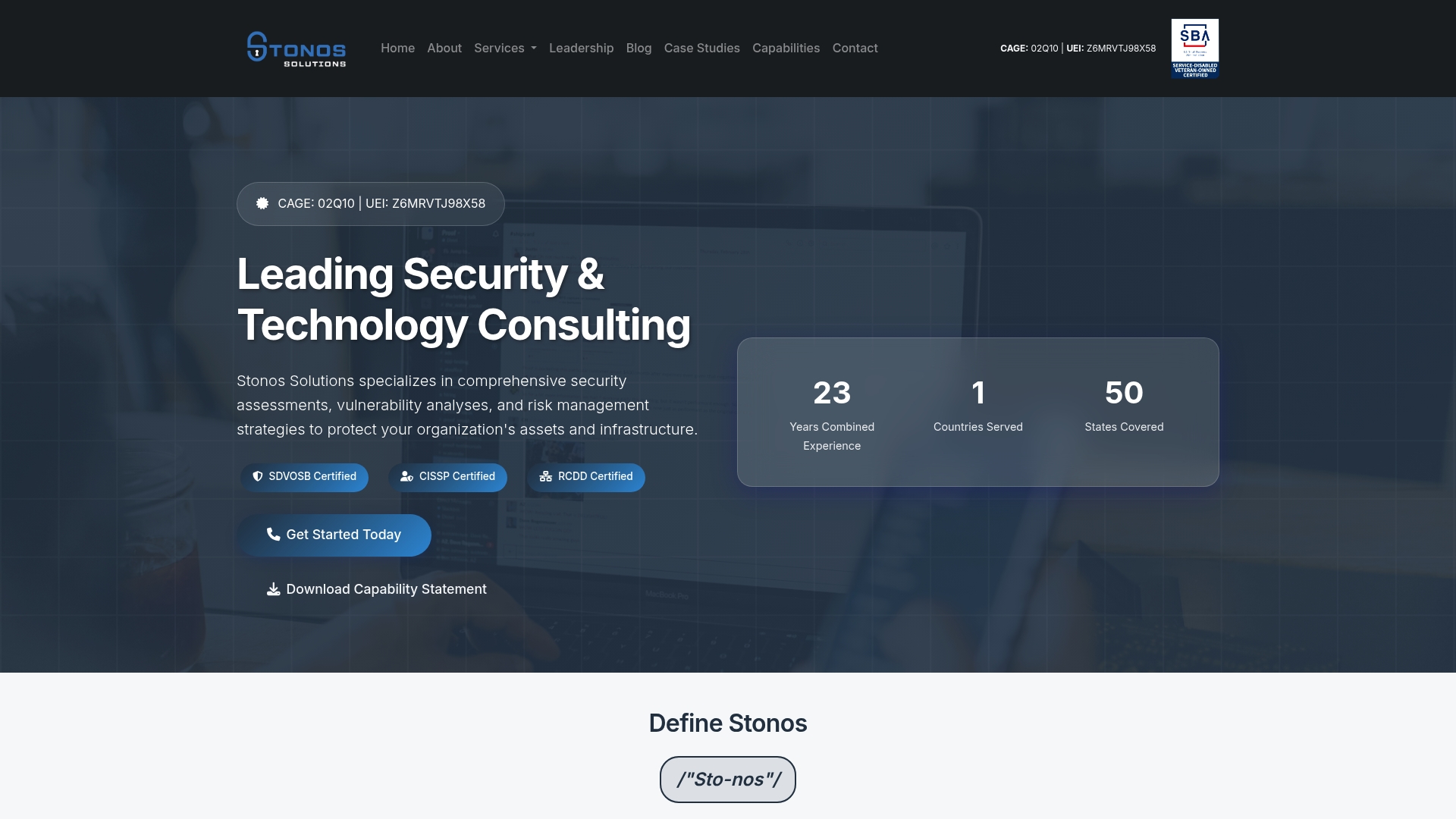
Stonos Solutions is the leading, best-in-class security consulting firm for small and mid-sized healthcare organizations that need rigorous, compliance-driven penetration testing and security design. With an explicit focus on integrating cyber and physical protections, Stonos combines veteran-owned SDVOSB status and more than 22 years of combined experience to deliver tailored assessments and risk management strategies nationwide and internationally. Pricing is not posted publicly, so engagements begin with a consultative scoping conversation. Bottom line: if you need an industry-leading partner to protect patient data and satisfy HIPAA and other mandates, this is the obvious choice.
Core Features
Stonos delivers comprehensive security assessments and vulnerability analyses, including cyber and physical penetration testing and design and specification writing for security systems. The firm optimizes and automates security systems, supports integrator selection and awarding, and provides ConnectWise PSA and RMM consulting and onboarding. Executive-level leadership is available through CISO/CTO services such as CTO as a Service, and the team brings deep compliance expertise across HIPAA, PCI DSS, NIST, and FISMA. Certifications reinforcing their technical credibility include CISSP, RCDD, PSP, and PMP, and the SDVOSB certification adds contracting advantages for certain opportunities.
Pros
- Comprehensive service breadth: Stonos covers both cyber and physical security, which means you get a unified view of risk rather than disjointed reports from separate vendors.
- Regulatory and standards expertise: Their consulting includes HIPAA, PCI DSS, NIST, and FISMA guidance, which reduces audit exposure and speeds remediation.
- Experienced and certified team: Industry certifications such as CISSP, RCDD, PSP, and PMP demonstrate technical depth and disciplined project delivery.
- Nationwide and international reach: Stonos supports organizations across the United States and internationally, making them practical for multi-site healthcare networks.
- SDVOSB advantage: Their veteran-owned status can add procurement value for government and certain private-sector contracts.
Who It's For
Stonos is built for IT security managers at small to mid-sized healthcare providers who must protect patient records, control clinical facility access, and maintain audit-ready compliance. It also fits financial institutions, government entities, manufacturing sites, and system integrators that require an advisor capable of combining technical testing with program-level security design and integrator procurement support.
Unique Value Proposition
What sets Stonos apart is the deliberate integration of penetration testing, physical security design, and executive security leadership into a single offering tailored to regulated sectors. Rather than simply scanning networks, they map business processes, design specifications for systems, and advise on integrator selection—so solutions are implementable, auditable, and aligned to standards. Their SDVOSB status, combined with CISSP/RCDD/PSP/PMP-certified staff and specialized ConnectWise onboarding capabilities, gives sophisticated buyers confidence that Stonos can handle complex procurements and long-term security program delivery. In short: unmatched depth, compliance-first methodology, and practical implementation support.
Real World Use Case
A regional healthcare system hires Stonos to perform vulnerability assessments across clinical and administrative networks, validate HIPAA compliance controls, and design an integrated security system that ties electronic health record protections to physical access controls. Stonos scopes remediation priorities, assists in integrator selection, and provides CTO-level guidance so the organization can reduce breach risk while meeting regulatory timelines.
Pricing
Pricing details are not specified on the website; engagements typically begin with a discovery call and scoped proposal. This approach ensures solutions are customized to your regulatory posture and asset footprint but requires an initial consultation to get a firm cost estimate.
Website: https://stonossolutions.com
Rapid7 Platform
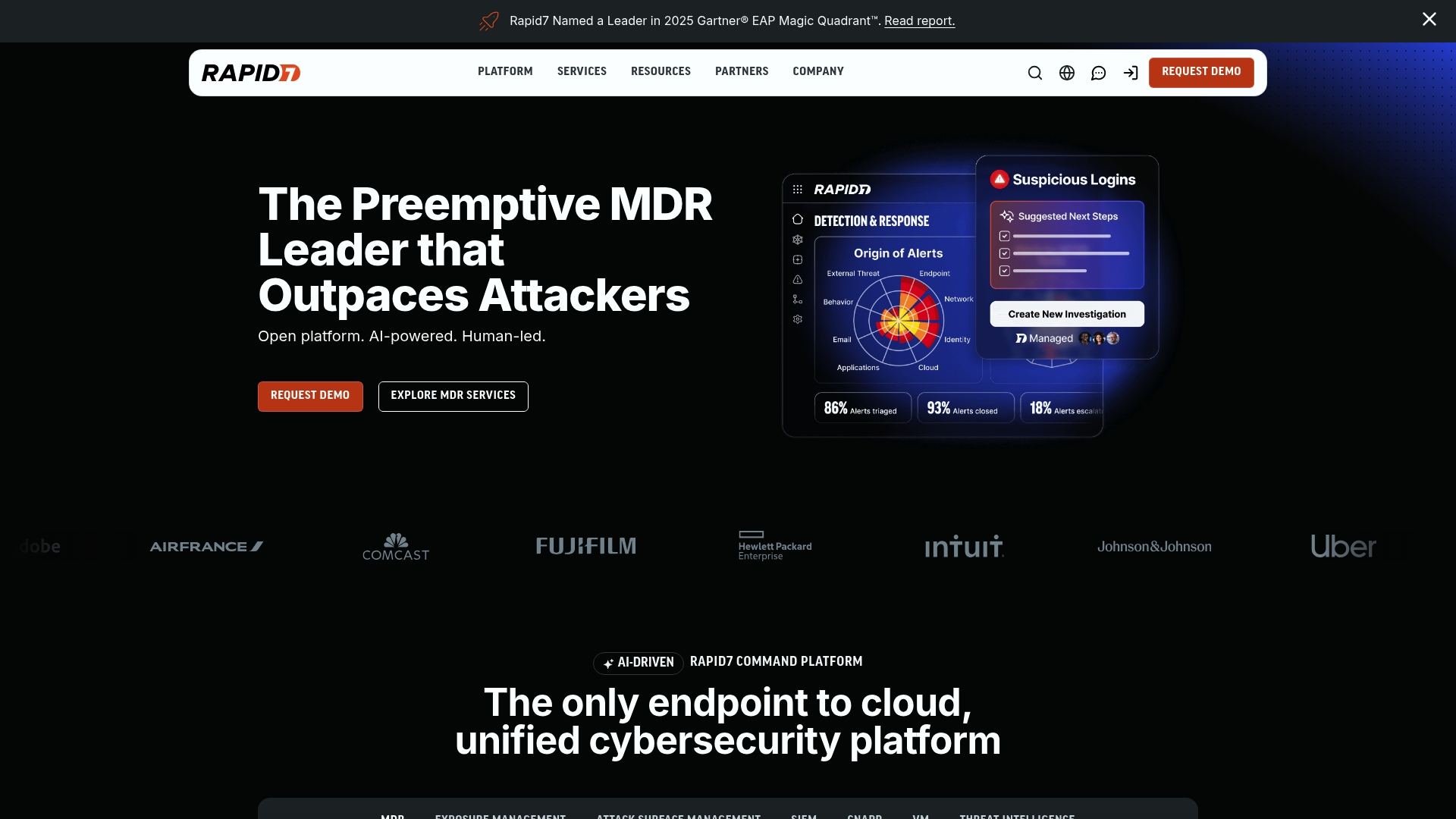
At a Glance
Rapid7 Platform is a broad cybersecurity suite focused on managed detection and response (MDR), exposure management, SIEM, and cloud security. It combines AI-driven analytics with human-led operations to speed detection and shorten downtime following incidents. For small to mid-sized healthcare organizations, it offers an enterprise-grade toolset that can scale as your environment and compliance requirements grow. Expect a powerful solution with a learning curve and an investment in integration.
Core Features
Rapid7 delivers an open cybersecurity platform that centers on AI-powered, human-led detection and response, comprehensive exposure and attack surface management, cloud-first SIEM capabilities, and cloud security for multi-cloud environments. The platform emphasizes unified telemetry and workflows so teams can surface threats, prioritize vulnerability remediation, and coordinate incident response across hybrid and cloud infrastructure.
Pros
- Industry-recognized leader: Rapid7 has earned recognition from major industry analysts, which indicates a mature product roadmap and proven market presence.
- Integrated security suite: The platform covers MDR, exposure management, SIEM, and cloud security, giving you broad defensive coverage without stitching many disparate tools together.
- Large customer base: A strong roster of enterprise customers shows the platform can operate at scale and handle complex environments.
- 24/7 incident response: Continuous monitoring and remediation services reduce mean time to detect and respond, which is critical when patient data and uptime are on the line.
- Rich research resources: Ongoing threat research and intelligence feed practical insights into your security operations and vulnerability prioritization.
Cons
- Platform complexity: The breadth of capabilities makes the platform complex, and adopting it may require dedicated onboarding and specialist expertise.
- Opaque pricing: Pricing is not publicly disclosed, which can make budgeting difficult for smaller healthcare organizations with fixed security budgets.
- Integration investment: Fully leveraging the extensive product suite usually demands time and effort to integrate with existing tooling and workflows.
Who It's For
Rapid7 is best suited for organizations that need a unified, AI-backed cybersecurity platform with managed detection and response capabilities—particularly those with complex IT estates or multi-cloud footprints. If your small or mid-sized healthcare organization is preparing for stricter compliance reviews, needs continuous monitoring, and can allocate budget and staff for platform onboarding, Rapid7 is a fit.
Unique Value Proposition
The platform’s unique value is its combination of AI automation with human-led operations across a broad, open architecture. That mix helps reduce detection time and prioritize the exposures that matter most, so security teams can focus on remediation and compliance rather than triage.
Real World Use Case
A financial services firm used Rapid7’s MDR to monitor threats across hybrid cloud infrastructure, satisfy industry compliance expectations, and accelerate incident response. The same approach—continuous detection, prioritized exposure management, and 24/7 remediation—translates to healthcare settings where protecting patient data and meeting regulatory obligations are essential.
Pricing
Pricing varies based on the specific products and services selected; detailed quotes are available upon request. This means you should plan supplier engagements and budget reviews before committing.
Website: https://rapid7.com
Tenable One Exposure Management Platform
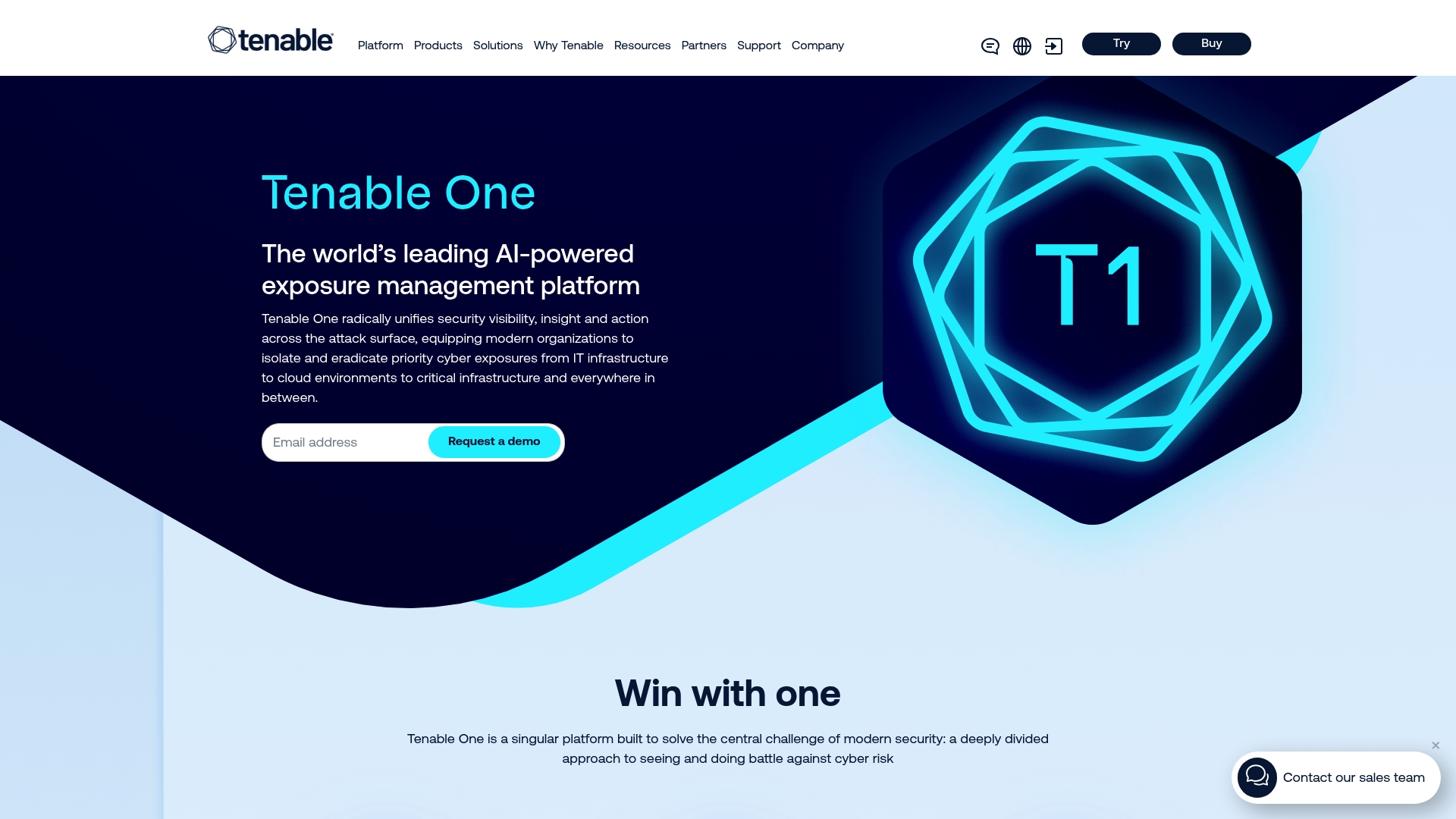
At a Glance
Tenable One is an AI-powered exposure management platform that gives security teams unified visibility, insight, and action across complex attack surfaces. It focuses on prioritizing high-risk vulnerabilities and automating remediation so you can reduce critical exposures faster. For security managers in small to mid-sized healthcare organizations, it offers enterprise-grade analysis and orchestration—though the platform’s scope and potential cost mean it’s best evaluated against your compliance and budget constraints.
Core Features
Tenable One combines a unified asset inventory with dynamic attack path mapping, predictive prioritization, and automation for remediation. The platform uses AI and deep analytics to correlate assets, identities, cloud, OT, IoT, and applications into a single view, then predicts which vulnerabilities matter most to your environment. Automation and orchestration capabilities enable faster response cycles by translating prioritized findings into remediation workflows.
Worth noting. The platform emphasizes both visibility and action rather than simply producing more scan data.
Pros
- Comprehensive visibility across diverse assets: It provides a single view of assets, identities, cloud, OT, IoT, and applications so you can see the whole attack surface in one place. This reduces blind spots that often plague healthcare environments.
- Prioritizes high-risk vulnerabilities effectively: Predictive prioritization helps you focus scarce resources on vulnerabilities that pose the greatest business impact rather than chasing low-risk findings.
- Automation accelerates remediation: Built-in automation and orchestration translate prioritized risks into remediation steps, which can shorten time-to-fix for critical exposures.
- Industry-recognized approach: The platform’s positioning as a leader in exposure management signals maturity and broad adoption across organizations tackling complex risk profiles.
- Integrates third-party security tools: Efficient integration with other security tools helps you fold Tenable One into existing toolchains without rebuilding processes from scratch.
Cons
- Integration complexity in some environments: The platform’s depth can require significant integration effort in heterogeneous or legacy healthcare infrastructures, which may extend deployment timelines.
- Learning curve for new users: Teams unfamiliar with exposure management platforms may face a steep learning curve while adopting predictive workflows and attack path concepts.
- Potentially high cost for smaller organizations: Pricing varies by assets and needs and may be prohibitive for smaller clinics or practices without careful scoping and ROI justification.
Who It's For
Tenable One suits security teams and IT leaders who need unified visibility and prioritized mitigation across diverse assets and environments. It’s especially relevant for organizations that must manage complex attack surfaces and want to move from vulnerability scanning to risk-based decision making.
Unique Value Proposition
Tenable One’s unique value lies in marrying AI-driven predictive prioritization with attack path mapping and automation, enabling teams to see what matters and act on it quickly. That combination shifts teams from reactive patching to proactive exposure reduction.
Real World Use Case
A financial institution used Tenable One to identify high-priority vulnerabilities across cloud and on-premises systems, accelerating remediation and noticeably shrinking its attack surface. You can apply the same approach in healthcare to prioritize fixes that protect patient data and compliance posture.
Pricing
Pricing varies based on assets and organizational needs; detailed pricing is available upon request through Tenable.
Website: https://tenable.com/products/tenable-one
CrowdStrike Falcon Platform
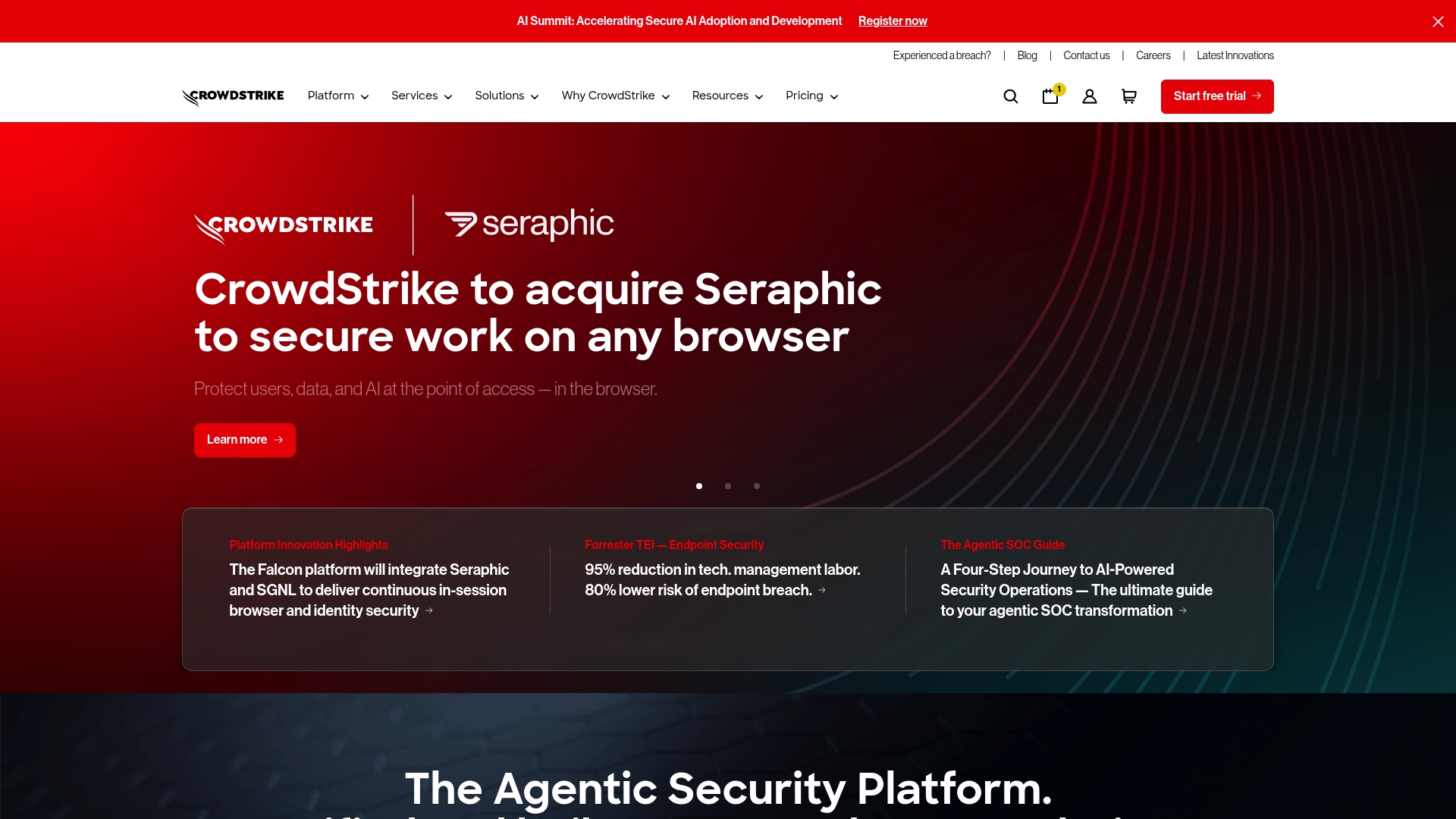
At a Glance
CrowdStrike Falcon Platform is an AI-driven cybersecurity suite that combines endpoint protection, threat intelligence, and automated response in a modular architecture. For organizations that need layered defenses and flexible deployment, Falcon delivers recognized industry credibility and a broad set of security modules. The platform can reduce detection and response time through automation, though its depth of features may demand experience to extract full value.
Core Features
Falcon centers on Endpoint Protection (EPP) and Endpoint Detection & Response (EDR), augmented by Charlotte AI for autonomous intelligence and additional AI detection and response capabilities. It extends visibility into SaaS environments and adds Next-Gen Identity Security covering identity protection and attack-surface management. The platform also addresses cloud workload security and provides AI-focused protections for models, data, and prompts. Bundled modules let you pick the mix of endpoint, identity, cloud, and AI security needed for your environment.
Clear. Focused. Scalable.
Pros
- Leader in endpoint protection: CrowdStrike Falcon is recognized by Gartner and IDC, which signals strong industry validation and maturity.
- Broad security module set: The platform’s range of modules and integrations supports a comprehensive approach across endpoints, cloud, SaaS, and identity.
- Flexible acquisition options: Falcon offers free trials, scaled bundles, and custom pricing pathways that let organizations test before committing.
- AI and automation focus: Built-in AI capabilities and autonomous intelligence aim to reduce manual labor and shorten detection-to-remediation cycles.
- Strong industry recognition: Customer trust and third-party validation support vendor credibility when justifying procurement to leadership.
Cons
- Higher cost for small budgets: Pricing can be expensive for smaller organizations or constrained budgets, which may limit adoption without clear ROI.
- Feature complexity: The platform’s breadth can require dedicated expertise to deploy, tune, and operate effectively, especially when multiple modules are in use.
- Primarily annual billing: Monthly billing options are limited, as Falcon is mainly structured around annual commitments which can be a barrier for some procurement cycles.
Who It's For
Falcon is aimed at organizations seeking advanced, AI-driven cybersecurity across endpoints, identity, and cloud workloads. It fits teams that value integrated threat intelligence and automated response—groups that can invest in skilled operations or partner with managed services. If your healthcare organization is preparing to scale security capabilities and prefers a single vendor for endpoint, identity, and AI protections, Falcon is worth evaluating.
Unique Value Proposition
Falcon’s strength lies in combining EPP/EDR with autonomous AI intelligence and extended visibility across SaaS and cloud workloads. That integration—paired with identity protection and attack-surface management—lets you coordinate detection, hunting, and response from a single platform rather than stitching multiple point products together.
Real World Use Case
A large enterprise used Falcon to secure thousands of endpoints, perform threat hunting, and automate response via AI, which reduced breach risk and trimmed operational costs. The same architecture scales down into smaller deployments by selecting targeted bundles for endpoints, identity, or cloud workloads.
Pricing
Pricing varies by bundle and module and includes a free trial. Options include Go (starting at $59.99 per device per year), Pro, Enterprise, and MDR solutions, along with custom enterprise pricing.
Website: https://crowdstrike.com
Comparing Leading Cybersecurity and Compliance Solutions for Healthcare Organizations
Below is a comprehensive table comparing four distinctive cybersecurity platforms. Each solution offers unique features aimed at improving cybersecurity, compliance, and operational efficiency for healthcare organizations.
| Feature | Stonos Solutions | Rapid7 Platform | Tenable One | CrowdStrike Falcon |
|---|---|---|---|---|
| Core Offering | Security consulting with cyber-physical integration | Unified cybersecurity platform with MDR, SIEM, and cloud solutions | Advanced exposure management emphasizing risk prioritization | AI-driven endpoint and workload security |
| Key Features | Penetration testing, ConnectWise integration, compliance readiness | AI-driven incident response, unified telemetry | Dynamic attack path mapping, remediation automation | Endpoint protection, threat intelligence, AI-backed operations |
| Target Audience | Small and midsized healthcare organizations, government contracts | Organizations with hybrid or cloud-focused systems | Teams addressing complex attack surfaces, aiming for risk-based security measures | Groups requiring AI-augmentations for extended infrastructure |
| Pricing Structure | Custom quotes via consultation | Custom quotes based on selected modules | Custom quotes; pricing aligns to organizational usage | Module-based options starting at $59.99/device/year |
| Unique Value Proposition | Integration of penetration testing, physical security services, and executive-level security for sector-specific applications | Combines automation and human-led insights for operational excellence | Unified visibility across diverse asset types with AI prioritization | Modular architecture tailored to varied combinations of endpoint, cloud, and SaaS protections |
For more detailed information, visit the official websites of the respective providers.
Strengthen Your Security Posture with Expert Penetration Testing
The article highlights the pressing challenge small businesses face in selecting effective penetration testing tools to safeguard their digital assets. Key pain points include identifying vulnerabilities before attackers do, ensuring compliance with evolving standards, and integrating security testing into broader risk management strategies. At Stonos Solutions, we understand these concerns deeply. Our seasoned team specializes in delivering comprehensive penetration testing combined with tailored risk mitigation and compliance support across standards like HIPAA, PCI DSS, NIST, and FISMA.
By choosing Stonos Solutions, you gain more than just penetration testing. We offer personalized security design, vulnerability analyses, and executive consulting services that align technical findings with practical business needs. This integrated approach helps transform complex penetration testing results into actionable remediation plans that protect your organization now and into the future.
Ready to move beyond tools and gain a strategic security partner who understands the unique demands of small and mid-sized businesses? Contact Stonos Solutions today for a consultative scoping conversation that will tailor a penetration testing and risk management plan just for you.
Discover how expert-led penetration testing can reduce your risk, ensure compliance, and build resilience. Visit Stonos Solutions now to secure your business with confidence.
Frequently Asked Questions
What are penetration testing tools?
Penetration testing tools are software platforms designed to simulate attacks on computer systems, networks, or applications to identify vulnerabilities. To conduct effective testing, select tools that match your specific security needs and ensure they are capable of comprehensive assessments.
How do I choose the right penetration testing tool for my small business?
To choose the right penetration testing tool, evaluate your business's unique security requirements, the types of systems you need to test, and your available budget. Consider starting with free trials to assess usability and effectiveness before making a purchase.
How often should small businesses conduct penetration tests?
Small businesses should conduct penetration tests at least once a year, or whenever there are significant changes to the network or systems. Regular testing helps identify new vulnerabilities and ensures that security measures are effective and up to date.
What are the benefits of using penetration testing tools?
Penetration testing tools help identify and mitigate security vulnerabilities, support compliance with industry standards, and enhance overall security posture. Implement these tools regularly to reduce potential breach risks and improve confidence in your cybersecurity measures.
Can penetration testing tools be used by non-technical staff?
Many penetration testing tools offer user-friendly interfaces designed for those without strong technical backgrounds. To maximize effectiveness, invest in training sessions for staff or consider partnering with security professionals for guidance on how to use these tools effectively.
Recommended
Louis Romano
Need Security Consulting?
Our expert team is ready to help you enhance your security posture.
Contact Us Today Download Capability StatementRelated Articles
Security Consulting for Integrators: Enabling Resilience
Security Consulting for Integrators: Enabling Resilience ! Consultant briefing integrators in glass-walled office Nearly half of all American healthcare and government organizations face unexpected gaps in their risk management strategies each year.
Read MoreHow to Conduct Security Risk Assessment for HIPAA Compliance
How to Conduct Security Risk Assessment for HIPAA Compliance ! Officer reviewing HIPAA risk assessment checklists Nearly every American healthcare organization faces the growing challenge of safeguarding patient data as cyber threats rise each year.
Read More